OPS245 Lab 3
!!!THIS LAB IS NOT READY YET!!!
In this lab we'll look at the simplest types of user management on a Linux system.
What's a user
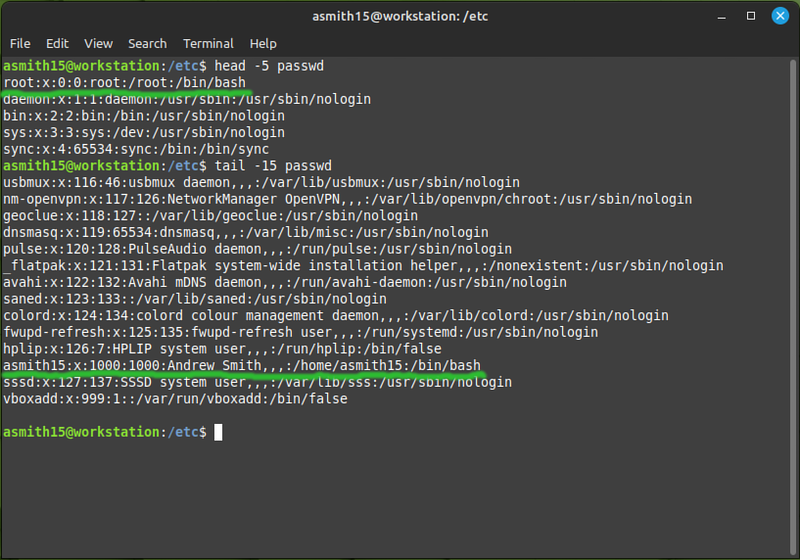
- Look at the contents of the /etc/passwd file:
Every line in that file is a user. Two of them you have used explicitly: root and your own username.
Each line is made of several fields, delimited by a colon. The same as a comma-separated value file (CSV) but separated by colons instead of commas. The fields are:
- The username (e.g. asmith15)
- A field that's no longer used, in the distant past it was the user's password
- The UID (user ID) - a unique number identifying the user. The system uses these numbers to determine who owns which files and processes.
- The GID (group ID) - the number identifying the user's primary group. Every user on a Linux system is a member of at least one group. It can be a member of other groups as well, but that membership is specified in the /etc/group file.
- A comment - an unstructured string of text, usually used to store a user's full name.
- The user's home directory. It's a sort of default directory for each user. You'll have noticed that it's the directory your shell is in when you log in, and it's what
~and$HOMEare set to. - The user's login shell. You would have only ever used Bash, but there are several other shells which some people prefer. The differences mostly matter only to advanced users.
The password
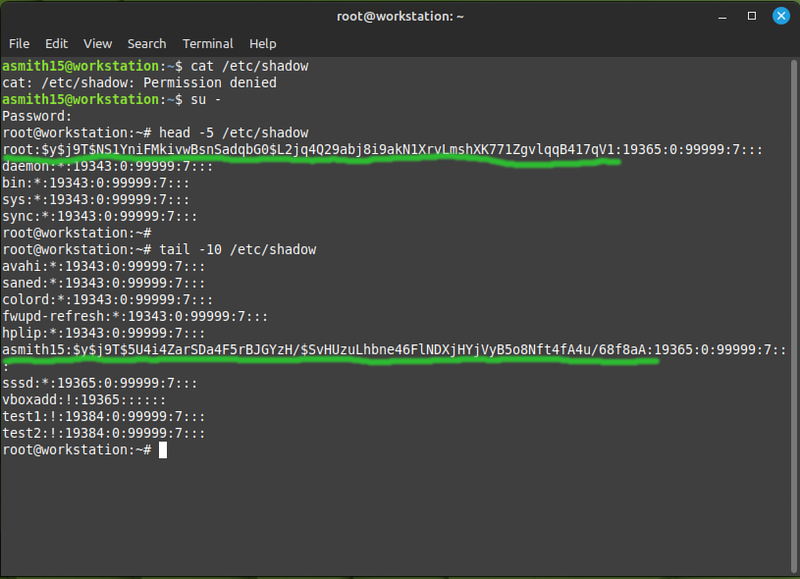
Linux users no longer have their hashed password stored in the passwd file. At one point the available computing power increased so much that the one-way hash could be reversed by brute force, therefore any user on the system could theoretically get any other user's password. To avoid this problem: the password hashes were moved to the /etc/shadow file which regular users don't have access to:
The long string of random-looking characters is not the password, it's a password hash. The idea with a hash is that you can convert some plain text into the hash, but you cannot convert the hash back into the plain text. You might think of it as encrypting something with no key to decrypt it, but it's a different process: a hash is a fixed size, and the data can be a million times larger than the hash - so it would be nonsensical to try and reverse the hashing process.