OPS245 Lab 7: Difference between revisions
(Created page with "= !!!THIS LAB IS NOT READY YET!!! = Computer security is a very large and complicated field, there are multi-year programs you could take just to get the basics. But we can get an introduction to some of the more obvious security issues you are likely to run into as a system administrator. = No security without hardware security = Depending on your experience you may already know that no bike lock can guarantee your bike won't get stolen, a locksmith can open any door...") |
|||
| Line 23: | Line 23: | ||
[[File:BootServer2FromMintISO.png|800px|border|center]] | [[File:BootServer2FromMintISO.png|800px|border|center]] | ||
* Boot up server2. Notice that the Linux Mint installation will come up. The original debian system is still on the harddrive, it's just not being used in this boot sequence. | |||
* Don't install Linux Mint, we're not trying to overwrite the old operating system. We're just going to bypass it in order to access some files. | |||
* Open a terminal and become root in that terminal. | |||
* Stop and think. Try to really understand the situation your system is in now. | |||
** You booted a machine you have physical access to (server2) using a live DVD. | |||
** The Live DVD does not require any sort of authentication, being an operating system installer. | |||
** The machine your booted has attached to it the storage devices used by the server2 operating system. | |||
** But the server2 operating system isn't even running now, so it can't possibly enforce any access limitations. | |||
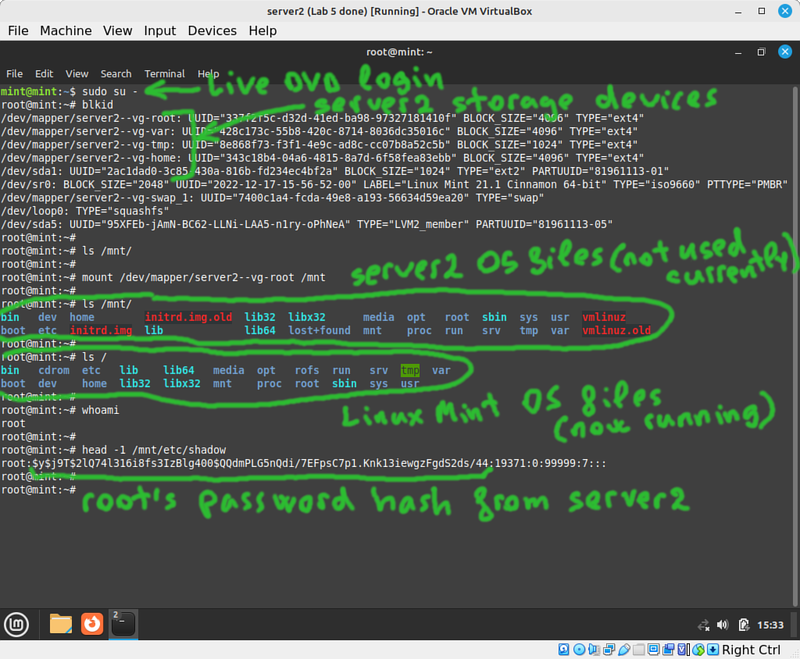
* Use <code>blkid</code> to see what block storage devices are currently available. | |||
* Since you're using LVM on server2 it's obvious which storage device is used for the root filesystem. Otherwise you might have had to try more than one filesystem to find which one was used for root. | |||
* Verify that /mnt is empty, and mount the root filesystem from server2 into the current /mnt directory. | |||
[[File:MountServer2Root.png|800px|border|center]] | |||
Revision as of 11:41, 20 March 2023
!!!THIS LAB IS NOT READY YET!!!
Computer security is a very large and complicated field, there are multi-year programs you could take just to get the basics. But we can get an introduction to some of the more obvious security issues you are likely to run into as a system administrator.
No security without hardware security
Depending on your experience you may already know that no bike lock can guarantee your bike won't get stolen, a locksmith can open any door without a key in seconds (or at most in minutes), and noone has yet come up with a way to prevent stealing a car.
In fact with very few exceptions anything can be broken into no matter how well the protection was designed, and how much it cost. The biggest strongest safe you can imagine can be cut into given the right tools and the time to do it.
Roughly the same applies to computers. You can implement any sort of security you like, but ultimately a determined attacker can break it if they can take your hardware apart. The only exception is a properly implemented encryption system using good keys, but even that can often be bypassed.
We'll use our server2 machine as an example to practice this.
- Boot up server2 normally, and log in as root.
- Create some secret files in root's home directory, and set their permissions so that only root can read them.
- You can set a very long and complicated password for root if you like, later you will see that it doesn't actually matter how good it is.
- Shut down server1 and make a snapshot of it just in case you make a mistake and damage something.
The trick we'll use in this case is to boot another operating system kernel on server1's hardware, and access server1's filesystem using that other operating system. That way we will bypassing any security that would have been enforced by server1's operating system kernel.
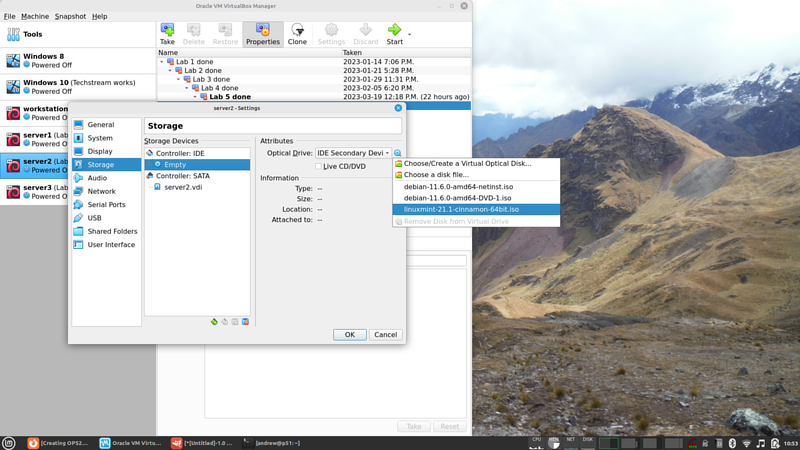
- In the VM's settings double-check that it will attempt to boot from a DVD before booting from the harddrive, then insert your Linux Mint ISO you used in the beginning of the course into server2's virtual optical drive:
- Boot up server2. Notice that the Linux Mint installation will come up. The original debian system is still on the harddrive, it's just not being used in this boot sequence.
- Don't install Linux Mint, we're not trying to overwrite the old operating system. We're just going to bypass it in order to access some files.
- Open a terminal and become root in that terminal.
- Stop and think. Try to really understand the situation your system is in now.
- You booted a machine you have physical access to (server2) using a live DVD.
- The Live DVD does not require any sort of authentication, being an operating system installer.
- The machine your booted has attached to it the storage devices used by the server2 operating system.
- But the server2 operating system isn't even running now, so it can't possibly enforce any access limitations.
- Use
blkidto see what block storage devices are currently available. - Since you're using LVM on server2 it's obvious which storage device is used for the root filesystem. Otherwise you might have had to try more than one filesystem to find which one was used for root.
- Verify that /mnt is empty, and mount the root filesystem from server2 into the current /mnt directory.