OPS345 Lab 7: Difference between revisions
No edit summary |
No edit summary |
||
| Line 1: | Line 1: | ||
= THIS PAGE IS A DRAFT, NOT READY FOR USE YET = | = THIS PAGE IS A DRAFT, NOT READY FOR USE YET = | ||
= SMTP Encryption = | |||
One thing we haven't spent time on last week is the connection from your email client to your email server. This will very often be on a very untrusted network, such as a free wifi you found in some random place. | |||
In this lab we'll set up your MTA to accept encrypted incomming connections, so that it won't matter what sort of network your workstation computer or phone is connected to. | |||
[[File:Email-servers.png|800px|border|center]] | |||
Sadly today there is still no widespread means to encrypt MTA->MTA SMTP connections, which means that fundamentally you cannot trust that your email hasn't been read or modified in transit. This is a problem we can't solve in this course, but we don't need to because it's a very large, global problem. A fix would require every single email server out there to comply with a brand new specfication which hasn't even been developed yet. | |||
* can't use the same keys generated in www lab, they're for the wrong FQDN | * can't use the same keys generated in www lab, they're for the wrong FQDN | ||
<source> | <source> | ||
| Line 82: | Line 92: | ||
* ss should show port 993, no 995 or 110 | * ss should show port 993, no 995 or 110 | ||
* there's no iptables running on email, so just open port 993 in ops345sgemail | * there's no iptables running on email, so just open port 993 in ops345sgemail | ||
* set up thunderbird for myseneca | |||
* configure thunderbird: | * configure thunderbird: | ||
** IMAP: email.asmith15.ops345.ca, SSL 993, normal password, username without @domain | ** IMAP: email.asmith15.ops345.ca, SSL 993, normal password, username without @domain | ||
| Line 95: | Line 106: | ||
* http://littlesvr.ca/grumble/2014/01/26/setting-up-sendmail-on-a-dynamic-ip-part2-spf/ | * http://littlesvr.ca/grumble/2014/01/26/setting-up-sendmail-on-a-dynamic-ip-part2-spf/ | ||
* Eventually the email you tried to send will bounce because that's a temporary error | * Eventually the email you tried to send will bounce because that's a temporary error | ||
*webmail | |||
[[Category:OPS345]] | [[Category:OPS345]] | ||
Revision as of 22:58, 14 March 2022
THIS PAGE IS A DRAFT, NOT READY FOR USE YET
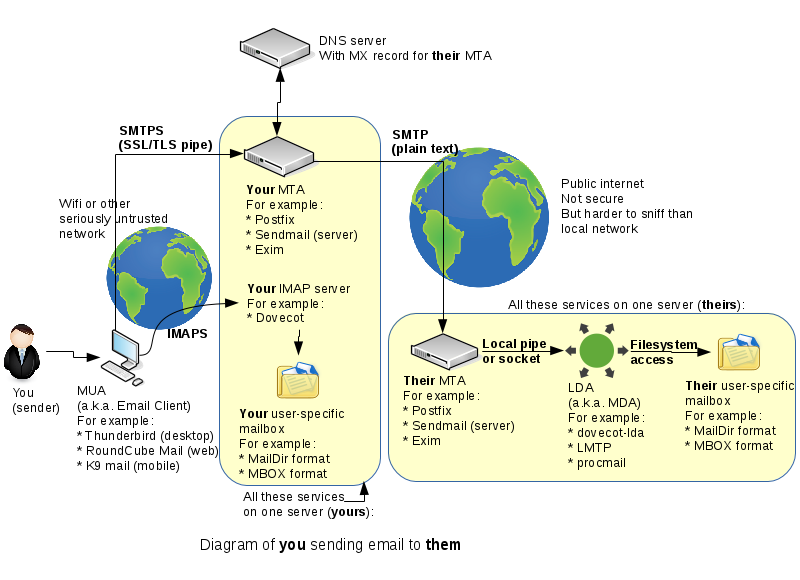
SMTP Encryption
One thing we haven't spent time on last week is the connection from your email client to your email server. This will very often be on a very untrusted network, such as a free wifi you found in some random place.
In this lab we'll set up your MTA to accept encrypted incomming connections, so that it won't matter what sort of network your workstation computer or phone is connected to.
Sadly today there is still no widespread means to encrypt MTA->MTA SMTP connections, which means that fundamentally you cannot trust that your email hasn't been read or modified in transit. This is a problem we can't solve in this course, but we don't need to because it's a very large, global problem. A fix would require every single email server out there to comply with a brand new specfication which hasn't even been developed yet.
- can't use the same keys generated in www lab, they're for the wrong FQDN
andrew@p51:~/prog/seneca/ops345/new$ sudo su -
root@p51:~# certonly --manual --preferred-challenges dns
certonly: command not found
root@p51:~# certbot certonly --manual --preferred-challenges dns
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Please enter in your domain name(s) (comma and/or space separated) (Enter 'c'
to cancel): email.asmith15.ops345.ca
Obtaining a new certificate
Performing the following challenges:
dns-01 challenge for email.asmith15.ops345.ca
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
NOTE: The IP of this machine will be publicly logged as having requested this
certificate. If you're running certbot in manual mode on a machine that is not
your server, please ensure you're okay with that.
Are you OK with your IP being logged?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.email.asmith15.ops345.ca with the following value:
PdK1vlZnYMdBO7untofSCkfXH2ejk3EE019R7A90x7Q
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/email.asmith15.ops345.ca/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/email.asmith15.ops345.ca/privkey.pem
Your cert will expire on 2022-02-28. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
root@p51:~# cp /etc/letsencrypt/live/email.asmith15.ops345.ca/cert.pem ~andrew/prog/seneca/ops345/new/keys/email.asmith15.ops345.ca.cert.pem
root@p51:~# cp /etc/letsencrypt/live/email.asmith15.ops345.ca/privkey.pem ~andrew/prog/seneca/ops345/new/keys/email.asmith15.ops345.ca.key.pem
root@p51:~# chown andrew ~andrew/prog/seneca/ops345/new/keys/email.asmith15.ops345.ca.*- Put keys on the email server:
scp -P 2212 -i keys/ssh/ops345-all-aws-machines.pem keys/email.asmith15.ops345.ca.* andrew@34.202.103.43:~
[root@email andrew]# cp email.asmith15.ops345.ca.cert.pem /etc/pki/tls/certs/
[root@email andrew]# cp email.asmith15.ops345.ca.key.pem /etc/pki/tls/private/- configure postfix to enable encrypted connections from client software. add this to the bottom of main.cf:
# Settings to enable secure SMTP using my self-signed certificate:
smtpd_tls_auth_only = no
smtpd_use_tls = yes
smtp_use_tls = yes
smtpd_tls_key_file = /etc/pki/tls/private/email.asmith15.ops345.ca.key.pem
smtpd_tls_cert_file = /etc/pki/tls/certs/email.asmith15.ops345.ca.cert.pem
tls_random_source = dev:/dev/urandom
smtpd_tls_loglevel = 1- test with telnet/EHLO: should say 250-STARTTLS
- complete test will be done with thunderbird later
- dovecot installed in previous lab, it needs very little configuration for our simple setup
- /etc/dovecot/dovecot.conf:
- Modify the protocols option so that Dovecot will work with IMAP connections, no POP3 or LMTP.
- 10-ssl.conf:
ssl_cert = </etc/pki/tls/certs/email.asmith15.ops345.ca.cert.pem
ssl_key = </etc/pki/tls/private/email.asmith15.ops345.ca.key.pem- ss should show port 993, no 995 or 110
- there's no iptables running on email, so just open port 993 in ops345sgemail
- set up thunderbird for myseneca
- configure thunderbird:
- IMAP: email.asmith15.ops345.ca, SSL 993, normal password, username without @domain
- SMTP: email.asmith15.ops345.ca, STARTTLS 25, normal password, username without @domain
- tail -f /var/log/maillog and send a message from thunderbird
- The message is not sent, because postfix is not configured to authenticate users. encryption alone is not enough.
- https://www.xmodulo.com/enable-user-authentication-postfix-smtp-server-sasl.html
- except the SSL/TLS parameters part.
- Send email again. Note the messages about connection timed out. We can't do anything about that in AWS Academy:
- There's more to do anyway to set up a real sending server, as a minimum DKIM/SPF but reverse DNS for the domain also helps.
- https://aws.amazon.com/premiumsupport/knowledge-center/route-53-reverse-dns/
- http://littlesvr.ca/grumble/2014/01/26/setting-up-sendmail-on-a-dynamic-ip-part2-spf/
- Eventually the email you tried to send will bounce because that's a temporary error
- webmail