OPS345 Lab 7: Difference between revisions
| Line 21: | Line 21: | ||
* Copy the two keys into the appropriate directories (/etc/pki/tls/certs/ and /etc/pki/tls/private/) on your email server. | * Copy the two keys into the appropriate directories (/etc/pki/tls/certs/ and /etc/pki/tls/private/) on your email server. | ||
== Configure Postfix == | |||
< | |||
As you did with Apache: you need to tell the email server (Postfix) to use your keys for encryption. There are also some other options you need to specify. None of these are in main.cf by default, so you can copy-paste them from here: | |||
<pre># Settings to enable secure SMTP using my key and certificate: | |||
smtpd_tls_auth_only = no | smtpd_tls_auth_only = no | ||
smtpd_use_tls = yes | smtpd_use_tls = yes | ||
| Line 30: | Line 33: | ||
tls_random_source = dev:/dev/urandom | tls_random_source = dev:/dev/urandom | ||
smtpd_tls_loglevel = 1 | smtpd_tls_loglevel = 1 | ||
</ | </pre> | ||
* test | |||
* After you restart Postfix and make sure it hasn't crashed due to a typo in the config file: test it. Use telnet to connect to it and look for 250-STARTTLS in its reply to your EHLO: | |||
[[File:AWSPostfix250Starttls.png|border|center]] | |||
That implies that your Postfix server is capable of setting up encrypted connections. We will test this later in the lab using Thunderbird. | |||
* dovecot installed in previous lab, it needs very little configuration for our simple setup | * dovecot installed in previous lab, it needs very little configuration for our simple setup | ||
* /etc/dovecot/dovecot.conf: | * /etc/dovecot/dovecot.conf: | ||
Revision as of 00:09, 15 March 2022
THIS PAGE IS A DRAFT, NOT READY FOR USE YET
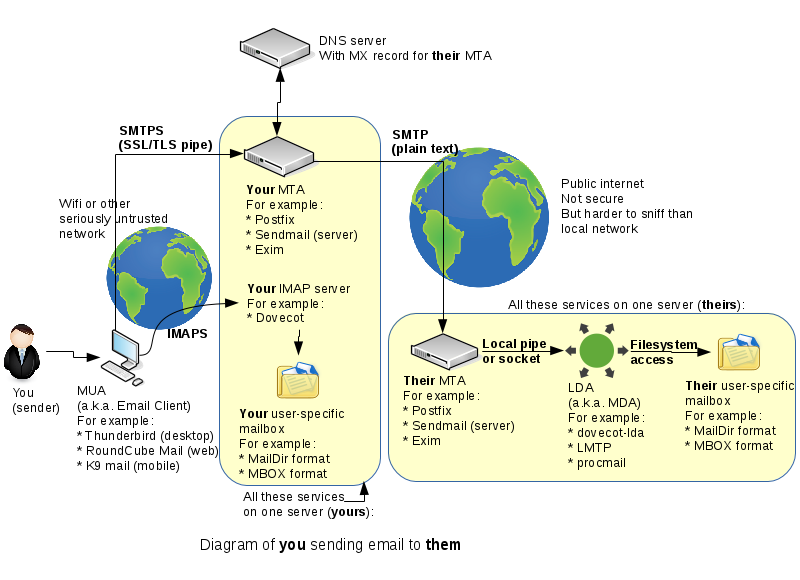
SMTP Encryption
One thing we haven't spent time on last week is the connection from your email client to your email server. This will very often be on a very untrusted network, such as a free wifi network you found in some random place.
In this lab we'll set up your MTA to accept encrypted incomming connections, so that it won't matter what sort of network your workstation computer or phone is connected to.
Sadly today there is still no widespread means to encrypt MTA->MTA SMTP connections, which means that fundamentally you cannot trust that your email hasn't been read or modified in transit. This is a problem we can't solve in this course, but we don't need to because it's a very large, global problem. A fix would require every single email server out there to comply with a brand new specfication which hasn't even been developed yet.
Generate encryption keys
You can't use the keys you've generated in lab 5 because they were tied to the hostname youruserid.ops345.ca, and the email server has a different FQDN: email.youruserid.ops345.ca.
- Use certbot again on your workstation to generate a key pair for email.youruserid.ops345.ca. Look at the lab 5 notes if you need a reminder for how to do it. But don't overwrite your web server's keys by mistake.
- Copy your new private key to ~yourusername/ops345/keys/certbot/email.yourusername.ops345.ca.key.pem on the workstation, for safekeeping.
- Copy your new certificate to ~yourusername/ops345/keys/certbot/email.yourusername.ops345.ca.cert.pem on the workstation, for safekeeping.
- Make sure the keys are owned by your regular user, not root.
- Copy the two keys into the appropriate directories (/etc/pki/tls/certs/ and /etc/pki/tls/private/) on your email server.
Configure Postfix
As you did with Apache: you need to tell the email server (Postfix) to use your keys for encryption. There are also some other options you need to specify. None of these are in main.cf by default, so you can copy-paste them from here:
# Settings to enable secure SMTP using my key and certificate: smtpd_tls_auth_only = no smtpd_use_tls = yes smtp_use_tls = yes smtpd_tls_key_file = /etc/pki/tls/private/email.asmith15.ops345.ca.key.pem smtpd_tls_cert_file = /etc/pki/tls/certs/email.asmith15.ops345.ca.cert.pem tls_random_source = dev:/dev/urandom smtpd_tls_loglevel = 1
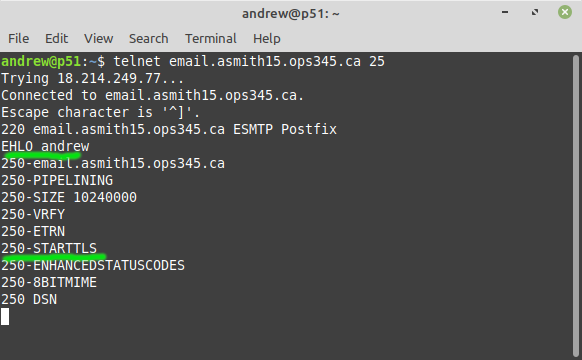
- After you restart Postfix and make sure it hasn't crashed due to a typo in the config file: test it. Use telnet to connect to it and look for 250-STARTTLS in its reply to your EHLO:
That implies that your Postfix server is capable of setting up encrypted connections. We will test this later in the lab using Thunderbird.
- dovecot installed in previous lab, it needs very little configuration for our simple setup
- /etc/dovecot/dovecot.conf:
- Modify the protocols option so that Dovecot will work with IMAP connections, no POP3 or LMTP.
- 10-ssl.conf:
ssl_cert = </etc/pki/tls/certs/email.asmith15.ops345.ca.cert.pem
ssl_key = </etc/pki/tls/private/email.asmith15.ops345.ca.key.pem- ss should show port 993, no 995 or 110
- there's no iptables running on email, so just open port 993 in ops345sgemail
- set up thunderbird for myseneca
- configure thunderbird:
- IMAP: email.asmith15.ops345.ca, SSL 993, normal password, username without @domain
- SMTP: email.asmith15.ops345.ca, STARTTLS 25, normal password, username without @domain
- tail -f /var/log/maillog and send a message from thunderbird
- The message is not sent, because postfix is not configured to authenticate users. encryption alone is not enough.
- https://www.xmodulo.com/enable-user-authentication-postfix-smtp-server-sasl.html
- except the SSL/TLS parameters part.
- Send email again. Note the messages about connection timed out. We can't do anything about that in AWS Academy:
- There's more to do anyway to set up a real sending server, as a minimum DKIM/SPF but reverse DNS for the domain also helps.
- https://aws.amazon.com/premiumsupport/knowledge-center/route-53-reverse-dns/
- http://littlesvr.ca/grumble/2014/01/26/setting-up-sendmail-on-a-dynamic-ip-part2-spf/
- Eventually the email you tried to send will bounce because that's a temporary error
- webmail