OPS345 Lab 6: Difference between revisions
No edit summary |
|||
| (2 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
= | = Encryption, certificates, etc. = | ||
Encryption means converting plain text (something you can read/use, it doesn't need to be text) into cyphertext. The cyphertext created by a good encryption algorithm is impossible (or, for weak algorithms: at least impractical) to decrypt (covert back into plain text) without a key. | |||
You've been using public key cryptography for your entire life (unless you were born before the 1990s). And you've been setting up public key cryptography for yourself since at least OPS245. If you actually understand how this stuff works: you'll be far ahead of the average sysadmin. | |||
We' | We don't have the time to do a comprehensive overview of cryptography, so I strongly encourage you to put the book '''Crypto''' by '''Steven Levy''' on your "must-read" list. Unfortunately they no longer have copies for check-out at the library, but I'm sure you can still find a way to read it. I have yet to see a better introduction to encryption. It's not a course reqirement - but if you don't want to be clueless about security fundamentals online - read that book and understand it. It reads like a novel, and it's perfectly readable even if you have no interest in math: | ||
[[Image:crypto.jpeg|center|"crypto" by Steven Levy]] | |||
In a nutshell, here are the most important points, the absolute minimum you need to be comfortable with this: | |||
* Public key encryption (also called assymetric encryption) uses two keys: a public key and a private key. | |||
* The two keys are permanently tied to each other by complex mathematics (read the book to get a feel for the fundamentals). You can't mix one public key with an unrelated private key. | |||
* The private key is like your password, you never give it to anyone. The public key is of no value to attackers, so there's no point in trying to protect it. | |||
* Anyone can encrypt something with the public key, but only the private key can be used to decrypt that. | |||
* Anyone can verify that a file signed using the private key has not been modified except by the owner of the private key. | |||
* A certificate is a public key typically signed by a third party's private key. | |||
* Symmetric encryption only has one private key, no public key. That makes it very hard to use with strangers on the internet. | |||
* Hashing is used a lot in cryptography, but it's not an encryption tool. | |||
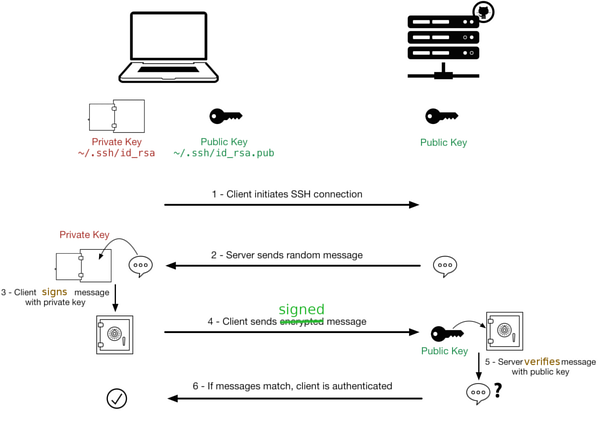
With those fundamentals you should be able to follow this diagram which describes how SSH key authentication works. The diagram is from Sébastien Saunier's blog (which is no longer online): | |||
[[Image:ssh_connection_explained.png|thumb|center|600px|A diagram explaining how public / private keys work.]] | |||
== Certificate Authorities (CAs) == | |||
The problem with assymetric encryption is the distribution of public keys. The encryption strength is meaningless if the client can't be sure it has the unmodified public key for the server. That's where a third party gets involved. This third party is called a Certificate Authority. | |||
The exact same concepts from the section above are used for CA-signed certificates. There's just a third party involved - which makes it seem like magic for too many people, including professionals in our field. | |||
If you have any ambitions in this field: set a goal for yourself to understand this stuff fully. At least eventually, if not now. | |||
=== Setup on the server === | |||
Let's take a web browser and web server for an example - since that's the most common use of this setup. | |||
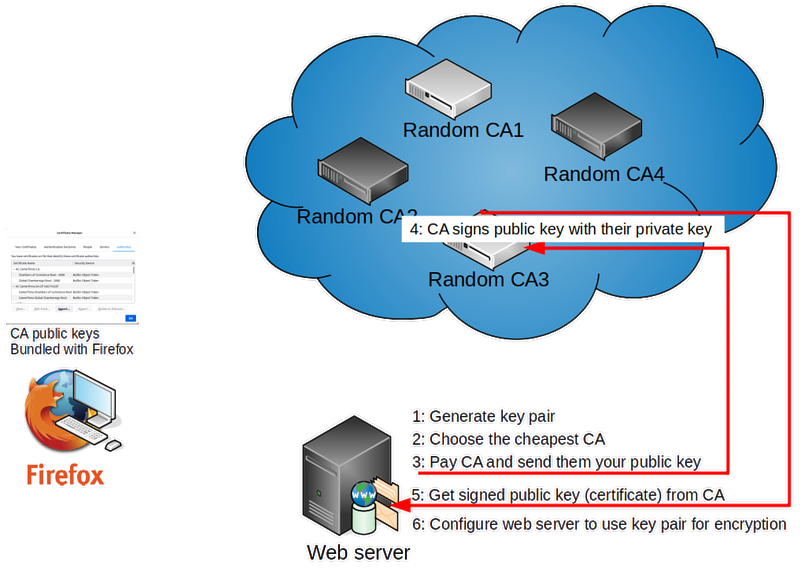
# First the web server administrator needs to generate a key pair, roughly the same as what you've been using for SSH (but using different commands). | |||
# The server admin needs to have the public key from that pair signed by a CA which browsers will accept as reliable. There are many such CAs, you can look in your browser's settings to see a full list. Typically people choose the cheapest option that will work in their setup. That's around 60$ a year. | |||
# The admin needs to pay the CA for the service. There's only one free option available which we'll use in this course. | |||
# The CA will use their private key to sign the web server's public key. That will allow people who already have the CA's public key to verify that the web server's public key has not been modified (by anyone other than the people who have access to any trusted CAs private key). | |||
# The server admin can download this signed public key (a.k.a. a certificate) from the CA. | |||
# The server admin will configure the web server to use the server's private key and the CA-signed version of its pair public key for secure communication over HTTPS. | |||
[[File:ServerCA.png|800px|border|center]] | |||
A certificate will always be linked to an FQDN. That mostly makes sense since web browsers connect to a web server using a domain name. Sometimes that's a pain in the neck for the administrator (you'll see why later) and the concept of "wildcard certificate" exists, but I was never able to set one up to work properly. | |||
=== Client communicating with server === | |||
Now that the server is configured, let's look at what happens when a web browser connects to a web server using HTTPS. | |||
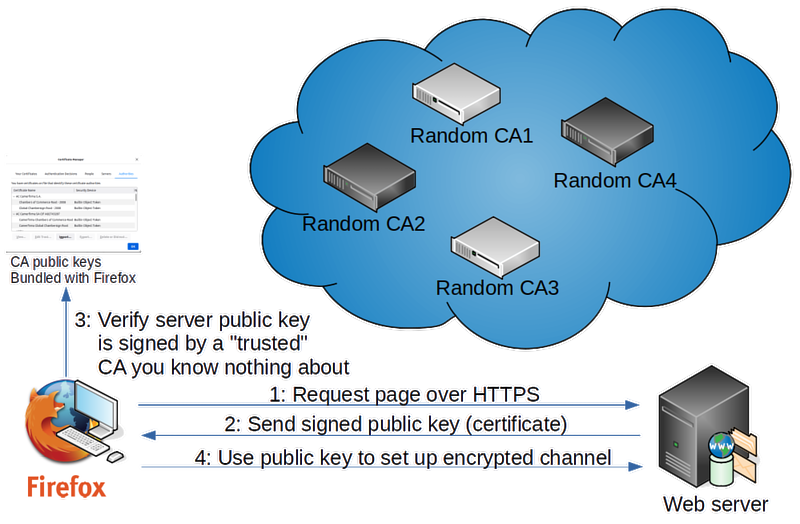
# The web browser connects to a web server, expecting to establish encrypted communication. | |||
# The web server will send to the client its CA-signed public key. | |||
# The browser came installed with a list of trusted CAs' public keys. Good luck figuring out how this list was compiled by whom when and how it's kept up to date. Let's just assume for now that those are all trustworthy, since everyone else assumes the same. It uses the appropriate CA's public key from that list to verify the server's public key. | |||
# At this point a combination of signing, encryption, and exchange of symmetrical encryption keys can be used to establish a connection where all traffic in both directions is encrypted. | |||
[[File:BrowserCA.png|800px|border|center]] | |||
== Self-signed certificates == | |||
Options exist if you need encrypted communication to your web or email server but you're not willing to pay for a CA or deal with the complexities required by Let's Encrypt: | |||
# You can self-sign a certificate, and add that certificate directly into your client software. If you have full control over all your client software: this is more secure and reliable than using a typical CA. | |||
# You can set up your own certificate authority (it takes one command to do that) to sign whatever certificates you want, and configure your client software to trust your CA. Again, this is more secure and reliable than relying on potentially untrustworthy CAs. | |||
We won't be doing either of those techniques in this course because their application requires closer knowledge of the business where they're used, and therefore it's too specific for this course. | |||
= HTTPS for your web server = | |||
We' | Generally-trusted CAs' services cost money. We're going to avoid extra costs in this course, and will use the one and only free CA which is trusted by a typical browser: '''Let's Encrypt'''. | ||
Let's Encrypt won't give you a certificate for more than 3 months, which is why the paid-for CAs still exist. They encourage you to set up automatic renewals of your certificate using their custom software, which is not always doable or even desireable. But it's free and 3 months is good enough for us. | |||
== | == Create your signed certificate == | ||
The steps below follow relevant instructions from the [https://help.datica.com/hc/en-us/articles/360044373551-Creating-and-Deploying-a-LetsEncrypt-Certificate-Manually Let's Encrypt Creating and Deploying a LetsEncrypt Certificate Manually] page. | |||
* Install certbot in your workstation using apt or the Software Manager. This is a command-line-only application. | |||
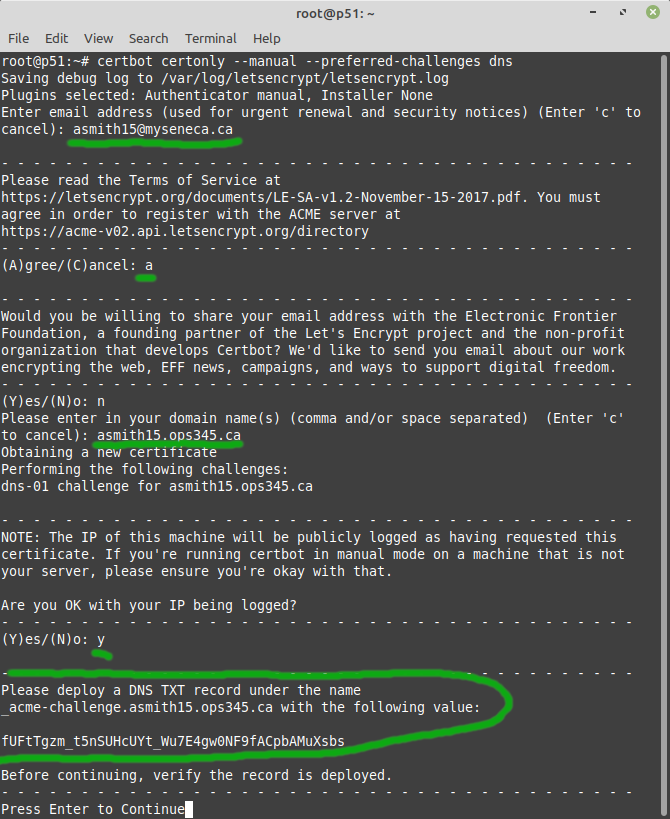
* Run <syntaxhighlight lang="bash">certbot certonly --manual --preferred-challenges dns</syntaxhighlight> as root. This will generate a key pair on your workstation, for your domain. Replace asmith15.ops345.ca with the domain that's correct for you. The output below is cut off after the notice to publish the TXT record: | |||
* | [[File:AWSCertbot-part1.png|border|center]] | ||
* | |||
* | Let's Encrypt verifies that you're authorized to get a certificate for yourusername.ops345.ca by asking you to add a TXT record under that domain. It's a reasonable assumption that if you have control over the DNS records for a domain: it's your domain. | ||
* | |||
* Leave the terminal running certbot and go to Bindistrar to add the TXT record Let's Encrypt asked for. | |||
* To avoid mistakes getting cached: double-check your record, then test it in another terminal on your workstation:<syntaxhighlight lang="bash">dig _acme-challenge.asmith15.ops345.ca TXT</syntaxhighlight> | |||
* If there is a mistake: note the TTL, it will make it hard for you to check that you fixed it correctly. But you can query the authoritative server for ops345.ca directly:<syntaxhighlight lang="bash">dig _acme-challenge.asmith15.ops345.ca TXT @littlesvr.ca</syntaxhighlight> | |||
* Once it looks good to you: press Enter in the terminal running certbot: | |||
[[File:AWSCertbot-part2.png|border|center]] | |||
* If that looks good: you can delete the TXT record from your DNS, it was only needed for a single use. | |||
* Save your private key and the certificate in your home directory to make them easier to find later and easier to back up:<syntaxhighlight lang="bash">mkdir -p ~yourusername/ops345/keys/certbot | |||
cp /etc/letsencrypt/live/yourusername.ops345.ca/privkey.pem ~yourusername/ops345/keys/certbot/yourusername.ops345.ca.key.pem | |||
cp /etc/letsencrypt/live/yourusername.ops345.ca/cert.pem ~yourusername/ops345/keys/certbot/yourusername.ops345.ca.cert.pem | |||
chown -R yourusername ~yourusername/ops345/keys/certbot</syntaxhighlight> | |||
The file yourusername.ops345.ca.cert.pem is what a CA would send you after you paid them. It: | |||
* Is useless without its private key pair. | |||
* Is not tied to the workstation you used to create it. | |||
* Is not tied to any particular service (e.g. Apache). | |||
* Is tied to the yourusername.ops345.ca domain. | |||
* Will become useless after it expires. | |||
== Set up Apache to use your new keys == | |||
Do this part of the lab on your www.yourusername.ops345.ca machine only. No need to touch the slaves you created in the assignment. | |||
* Remember that your keys are tied to a domain, so make sure that the ServerName option in /etc/httpd/conf/httpd.conf is set to your full domain name yourusername.ops345.ca | |||
* Apache can be configured to provide service over HTTPS relatively easily once you have the keys you need, but on Amazon Linux the SSL apache module is not installed by default, so install it now on your www server (give the machine a temporary elastic IP to allow yum to work, and release it after you're done):<syntaxhighlight lang="bash">yum install mod_ssl</syntaxhighlight> | |||
* Both your private key and your certificate need to be on the server because Apache needs to use them both. Use scp to copy them from your workstation to the server, and then copy them into the directories commonly used for this purpose: | |||
[[File:AWSCopyCertbotKeys.png|800px|border|center]] | |||
* Configure Apache to use those keys by setting the following two parameters in /etc/httpd/conf.d/ssl.conf:<syntaxhighlight lang="ApacheConf">SSLCertificateFile /etc/pki/tls/certs/yourusername.ops345.ca.cert.pem | |||
SSLCertificateKeyFile /etc/pki/tls/private/yourusername.ops345.ca.key.pem</syntaxhighlight> | |||
* Restart apache and confirm that there are no errors in /var/log/httpd/error_log nor in /var/log/httpd/ssl_error_log | |||
* Configure your firewalls and port forwarder to handle HTTPS, which works over TCP port 443: | |||
** Add an iptables rule in the nat table on router. | |||
** Add a rule for HTTPS in the router's security group to allow access from anywhere. | |||
** Add a rule for HTTPS in www's security group to allow access from the router only. | |||
* Test it in Firefox. It should work well for https://yourusername.ops345.ca and not well for https://www.yourusername.ops345.ca | |||
[[File:AWSHTTPSWorks.png|800px|border|center]] | |||
The problem with https://www.yourusername.ops345.ca is that your certificate is for a different domain. There are several different ways to deal with that, but we're not going to fix it. | |||
= Submit evidence of your work = | = Submit evidence of your work = | ||
| Line 112: | Line 127: | ||
For this lab, please submit screenshots that show you've completed the work, unless your professor has given you different instructions. As a minimum that's: | For this lab, please submit screenshots that show you've completed the work, unless your professor has given you different instructions. As a minimum that's: | ||
* | * Firefox showing https://yourusername.ops345.ca, or better yet https://yourusername.ops345.ca/nextcloud/ | ||
[[Category:OPS345]] | [[Category:OPS345]] | ||
Latest revision as of 13:10, 21 August 2023
Encryption, certificates, etc.
Encryption means converting plain text (something you can read/use, it doesn't need to be text) into cyphertext. The cyphertext created by a good encryption algorithm is impossible (or, for weak algorithms: at least impractical) to decrypt (covert back into plain text) without a key.
You've been using public key cryptography for your entire life (unless you were born before the 1990s). And you've been setting up public key cryptography for yourself since at least OPS245. If you actually understand how this stuff works: you'll be far ahead of the average sysadmin.
We don't have the time to do a comprehensive overview of cryptography, so I strongly encourage you to put the book Crypto by Steven Levy on your "must-read" list. Unfortunately they no longer have copies for check-out at the library, but I'm sure you can still find a way to read it. I have yet to see a better introduction to encryption. It's not a course reqirement - but if you don't want to be clueless about security fundamentals online - read that book and understand it. It reads like a novel, and it's perfectly readable even if you have no interest in math:
In a nutshell, here are the most important points, the absolute minimum you need to be comfortable with this:
- Public key encryption (also called assymetric encryption) uses two keys: a public key and a private key.
- The two keys are permanently tied to each other by complex mathematics (read the book to get a feel for the fundamentals). You can't mix one public key with an unrelated private key.
- The private key is like your password, you never give it to anyone. The public key is of no value to attackers, so there's no point in trying to protect it.
- Anyone can encrypt something with the public key, but only the private key can be used to decrypt that.
- Anyone can verify that a file signed using the private key has not been modified except by the owner of the private key.
- A certificate is a public key typically signed by a third party's private key.
- Symmetric encryption only has one private key, no public key. That makes it very hard to use with strangers on the internet.
- Hashing is used a lot in cryptography, but it's not an encryption tool.
With those fundamentals you should be able to follow this diagram which describes how SSH key authentication works. The diagram is from Sébastien Saunier's blog (which is no longer online):
Certificate Authorities (CAs)
The problem with assymetric encryption is the distribution of public keys. The encryption strength is meaningless if the client can't be sure it has the unmodified public key for the server. That's where a third party gets involved. This third party is called a Certificate Authority.
The exact same concepts from the section above are used for CA-signed certificates. There's just a third party involved - which makes it seem like magic for too many people, including professionals in our field.
If you have any ambitions in this field: set a goal for yourself to understand this stuff fully. At least eventually, if not now.
Setup on the server
Let's take a web browser and web server for an example - since that's the most common use of this setup.
- First the web server administrator needs to generate a key pair, roughly the same as what you've been using for SSH (but using different commands).
- The server admin needs to have the public key from that pair signed by a CA which browsers will accept as reliable. There are many such CAs, you can look in your browser's settings to see a full list. Typically people choose the cheapest option that will work in their setup. That's around 60$ a year.
- The admin needs to pay the CA for the service. There's only one free option available which we'll use in this course.
- The CA will use their private key to sign the web server's public key. That will allow people who already have the CA's public key to verify that the web server's public key has not been modified (by anyone other than the people who have access to any trusted CAs private key).
- The server admin can download this signed public key (a.k.a. a certificate) from the CA.
- The server admin will configure the web server to use the server's private key and the CA-signed version of its pair public key for secure communication over HTTPS.
A certificate will always be linked to an FQDN. That mostly makes sense since web browsers connect to a web server using a domain name. Sometimes that's a pain in the neck for the administrator (you'll see why later) and the concept of "wildcard certificate" exists, but I was never able to set one up to work properly.
Client communicating with server
Now that the server is configured, let's look at what happens when a web browser connects to a web server using HTTPS.
- The web browser connects to a web server, expecting to establish encrypted communication.
- The web server will send to the client its CA-signed public key.
- The browser came installed with a list of trusted CAs' public keys. Good luck figuring out how this list was compiled by whom when and how it's kept up to date. Let's just assume for now that those are all trustworthy, since everyone else assumes the same. It uses the appropriate CA's public key from that list to verify the server's public key.
- At this point a combination of signing, encryption, and exchange of symmetrical encryption keys can be used to establish a connection where all traffic in both directions is encrypted.
Self-signed certificates
Options exist if you need encrypted communication to your web or email server but you're not willing to pay for a CA or deal with the complexities required by Let's Encrypt:
- You can self-sign a certificate, and add that certificate directly into your client software. If you have full control over all your client software: this is more secure and reliable than using a typical CA.
- You can set up your own certificate authority (it takes one command to do that) to sign whatever certificates you want, and configure your client software to trust your CA. Again, this is more secure and reliable than relying on potentially untrustworthy CAs.
We won't be doing either of those techniques in this course because their application requires closer knowledge of the business where they're used, and therefore it's too specific for this course.
HTTPS for your web server
Generally-trusted CAs' services cost money. We're going to avoid extra costs in this course, and will use the one and only free CA which is trusted by a typical browser: Let's Encrypt.
Let's Encrypt won't give you a certificate for more than 3 months, which is why the paid-for CAs still exist. They encourage you to set up automatic renewals of your certificate using their custom software, which is not always doable or even desireable. But it's free and 3 months is good enough for us.
Create your signed certificate
The steps below follow relevant instructions from the Let's Encrypt Creating and Deploying a LetsEncrypt Certificate Manually page.
- Install certbot in your workstation using apt or the Software Manager. This is a command-line-only application.
- Run as root. This will generate a key pair on your workstation, for your domain. Replace asmith15.ops345.ca with the domain that's correct for you. The output below is cut off after the notice to publish the TXT record:
certbot certonly --manual --preferred-challenges dns
Let's Encrypt verifies that you're authorized to get a certificate for yourusername.ops345.ca by asking you to add a TXT record under that domain. It's a reasonable assumption that if you have control over the DNS records for a domain: it's your domain.
- Leave the terminal running certbot and go to Bindistrar to add the TXT record Let's Encrypt asked for.
- To avoid mistakes getting cached: double-check your record, then test it in another terminal on your workstation:
dig _acme-challenge.asmith15.ops345.ca TXT
- If there is a mistake: note the TTL, it will make it hard for you to check that you fixed it correctly. But you can query the authoritative server for ops345.ca directly:
dig _acme-challenge.asmith15.ops345.ca TXT @littlesvr.ca
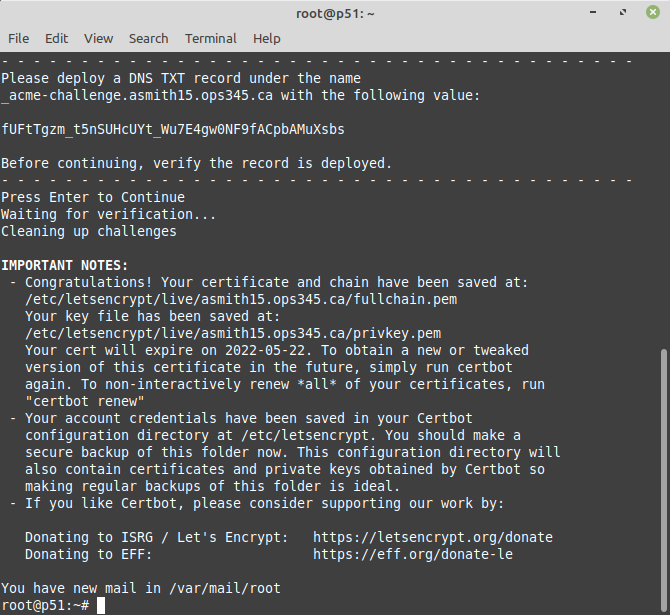
- Once it looks good to you: press Enter in the terminal running certbot:
- If that looks good: you can delete the TXT record from your DNS, it was only needed for a single use.
- Save your private key and the certificate in your home directory to make them easier to find later and easier to back up:
mkdir -p ~yourusername/ops345/keys/certbot cp /etc/letsencrypt/live/yourusername.ops345.ca/privkey.pem ~yourusername/ops345/keys/certbot/yourusername.ops345.ca.key.pem cp /etc/letsencrypt/live/yourusername.ops345.ca/cert.pem ~yourusername/ops345/keys/certbot/yourusername.ops345.ca.cert.pem chown -R yourusername ~yourusername/ops345/keys/certbot
The file yourusername.ops345.ca.cert.pem is what a CA would send you after you paid them. It:
- Is useless without its private key pair.
- Is not tied to the workstation you used to create it.
- Is not tied to any particular service (e.g. Apache).
- Is tied to the yourusername.ops345.ca domain.
- Will become useless after it expires.
Set up Apache to use your new keys
Do this part of the lab on your www.yourusername.ops345.ca machine only. No need to touch the slaves you created in the assignment.
- Remember that your keys are tied to a domain, so make sure that the ServerName option in /etc/httpd/conf/httpd.conf is set to your full domain name yourusername.ops345.ca
- Apache can be configured to provide service over HTTPS relatively easily once you have the keys you need, but on Amazon Linux the SSL apache module is not installed by default, so install it now on your www server (give the machine a temporary elastic IP to allow yum to work, and release it after you're done):
yum install mod_ssl
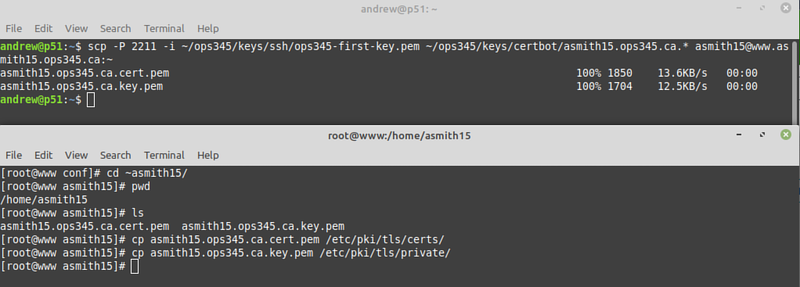
- Both your private key and your certificate need to be on the server because Apache needs to use them both. Use scp to copy them from your workstation to the server, and then copy them into the directories commonly used for this purpose:
- Configure Apache to use those keys by setting the following two parameters in /etc/httpd/conf.d/ssl.conf:
SSLCertificateFile /etc/pki/tls/certs/yourusername.ops345.ca.cert.pem SSLCertificateKeyFile /etc/pki/tls/private/yourusername.ops345.ca.key.pem
- Restart apache and confirm that there are no errors in /var/log/httpd/error_log nor in /var/log/httpd/ssl_error_log
- Configure your firewalls and port forwarder to handle HTTPS, which works over TCP port 443:
- Add an iptables rule in the nat table on router.
- Add a rule for HTTPS in the router's security group to allow access from anywhere.
- Add a rule for HTTPS in www's security group to allow access from the router only.
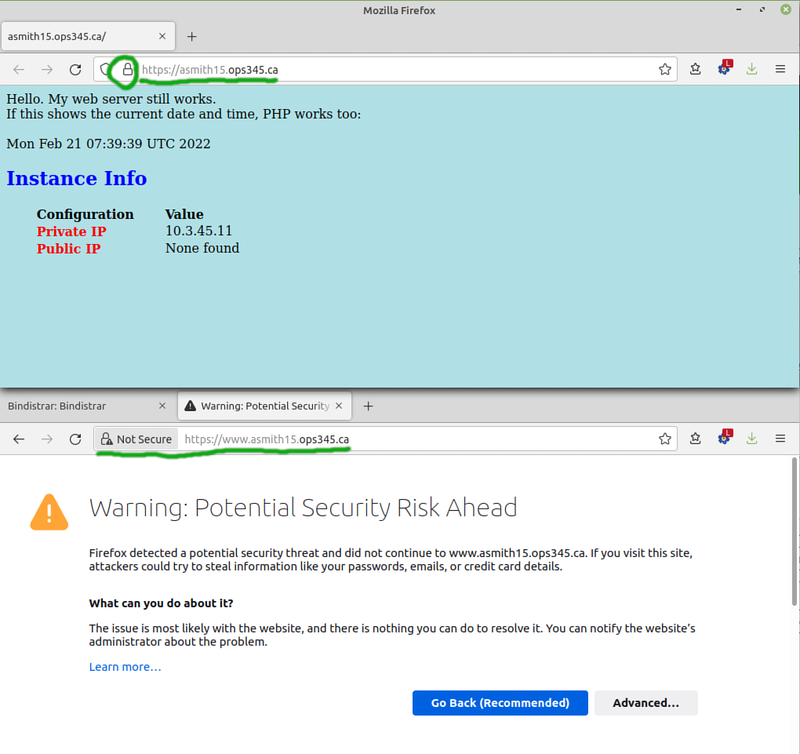
- Test it in Firefox. It should work well for https://yourusername.ops345.ca and not well for https://www.yourusername.ops345.ca
The problem with https://www.yourusername.ops345.ca is that your certificate is for a different domain. There are several different ways to deal with that, but we're not going to fix it.
Submit evidence of your work
For this lab, please submit screenshots that show you've completed the work, unless your professor has given you different instructions. As a minimum that's:
- Firefox showing https://yourusername.ops345.ca, or better yet https://yourusername.ops345.ca/nextcloud/